This will be a step by step process to migrate Active Directory Certificate Services from one server to another in same domain. It is a case when you upgrade or change your server where CA is installed.
You have to know some basic things before you begin to migrate a CA server:
- It is recommended that the new server has the same name as old one – this because we have CRL and other paths in certificates. If this name is not accessible, we can’t control the validity of the certificate.
- This is not a migration from one server to another; we have to export all settings and backups from the old server, demount it and after this install the new one with the same name. Errors and mistakes are not allowed.
- Do the migration slowly, take your time, document everything. You will need all the documentation during the migration and supporting period.
- In this guide, you will find steps to migrate one server. If you have a more complicated environment with more servers and subordinary CAs, then you need plans for migration of the entire migration before you start the migration.
Source server
First take full backup of the entire server. This step is non mandatory, but you may need it if something goes wrong.
After this check and write down the server name, IP address (if is static), paths where CA database and CRL are located. You will need this data to restore the same configuration on the new server.
Now, the crucial step is to make a backup of all certificates, certificate templates, settings, databases, root CA and registry settings. Unfortunately, CA backup does not care about all settings – it will backup only the CA database. Steps that are required to be able to transfer the entire configuration are:
- Check all the roles that are installed (CA, CA Web enrolment…) because you will need to install the same roles on the destination server.
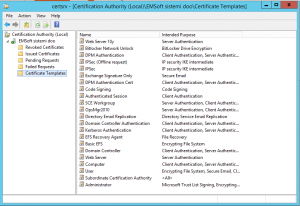
- In MMC (mmc.exe) open the Certificate Authority snap in and take a screenshot or write down the names of certificate templates you are using. When you will install the new server, you will have to enable same templates. You can export all certificate template names also with command certutil.exe –catemplates > D:\Backup\catemplates.txt from administrative Command prompt. This step is required only if you are using enterprise CA.
- Now, that we have the CA opened in MMC, we can also use it to backup CA database. To do this right click on CA server name, go to All tasks and select Back up CA. Follow the wizard and be careful that you select Private key and CA certificate and Certificate database and certificate database log check boxes. Only in this way you will backup all data that we need.
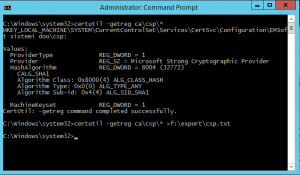
- Record your CAs CSP and signature algorithm. This can be done by executing command certutil.exe –getreg ca\csp\* > d:\Backup\csp.txt from administrative Command prompt. There will be nothing to do later if you are using default algorithms, but is always better to check.
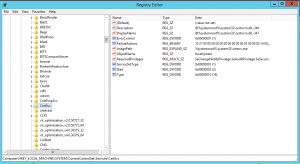
- Export the registry keys: on destination server you will need to have the same settings as you had on source, so you need to export registry separately because this is not a part of CA backup procedure. Open Regedit.exe and navigate to HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration. Right click to key and save it to file.
- If you are using custum policy, you should include it into backup. This means that you have to copy the file CAPolicy.inf that is located in C:\Windows (System root folder).
- Review all steps to check if they are done correctly!
- Using server manager remove CA roles from the server and restart the server.
- Remove server from domain, restart it and at the end turn it off. If you have other roles on the same server, you also have to move them on other servers. From this point your old server is down – you don’t need it anymore.