In past I already wrote about resetting Administrator password in this post. That was perfect for Windows 10 (till 1903) and Servers 2012 and 2016. Probably Microsoft was not really satisfied that users were able to “recover” lost passwords in such an easy way (this is my opinion). It is OK if these steps are used to reset your lost password, but not if you use them to reset a password from a stolen computer.
I think that this is the reason that you cannot rename cmd.exe in other executables and run it before you log in – for example to change the password. It makes sense, it is perfect for me as it is more secure. But someone forgot something: it is not a requirement to open CMD to use NET USER command, you can do it from PowerShell as well – and it’s working also in Server 2019!
Here are the steps (they are very similar as previous steps):
- Boot from DVD – you need to access to Windows system drive offline – installation DVD has all tools that you need.
- From menu select Repair your computer. This will give you the ability to change some files.
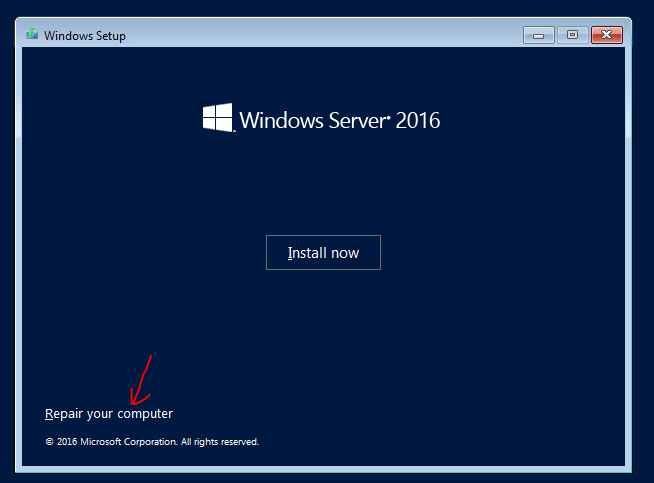
- In the next menu select Troubleshot.
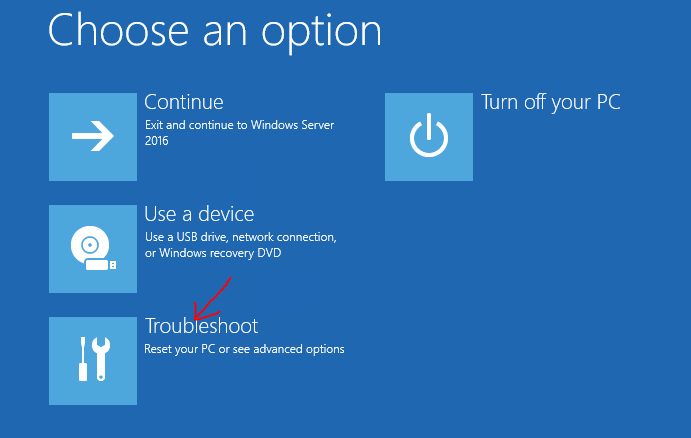
- Select Command prompt. This is what we need – we want to modify some files.
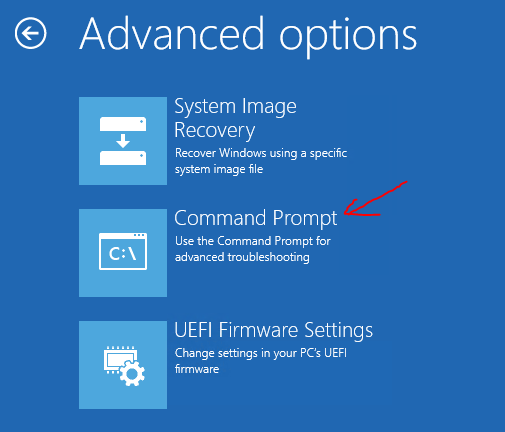
- Now you need to replace the file:
- Go to C: (supposing that C: is your system drive)
- Type cd \Windows\System32 – to enter into the folder
- Type ren osk.exe osk.old – be smart, you need to preserve the original file and put it back at the end of the process! If you don’t replace it again it means that you leave open a surface attack!!!
- Replace the file with a copy C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe osk.exe
- Reboot the server in normal mode.
- From the logon screen choose Onscreen keyboard (as in picture).
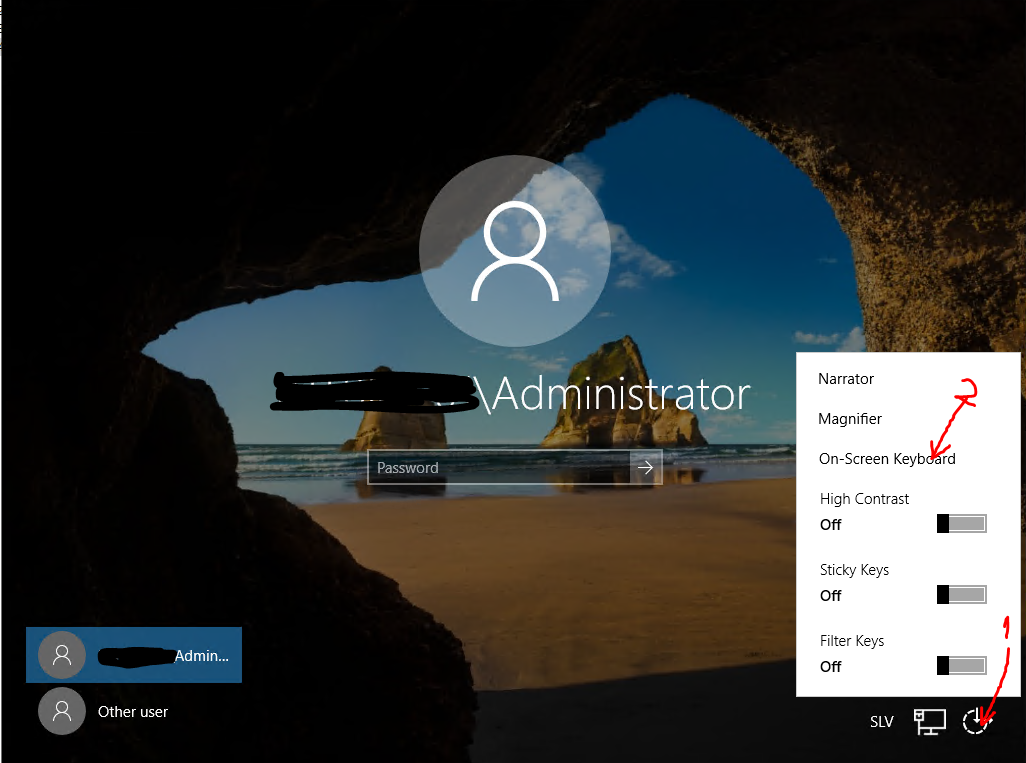
- PowerShell window will be opened – and you are a local system user!!! You can do a lot of things.
- Change the password with command Net user Administrator Password – where Administrator is the username of local or domain administrator and Password is the password that you want to set.
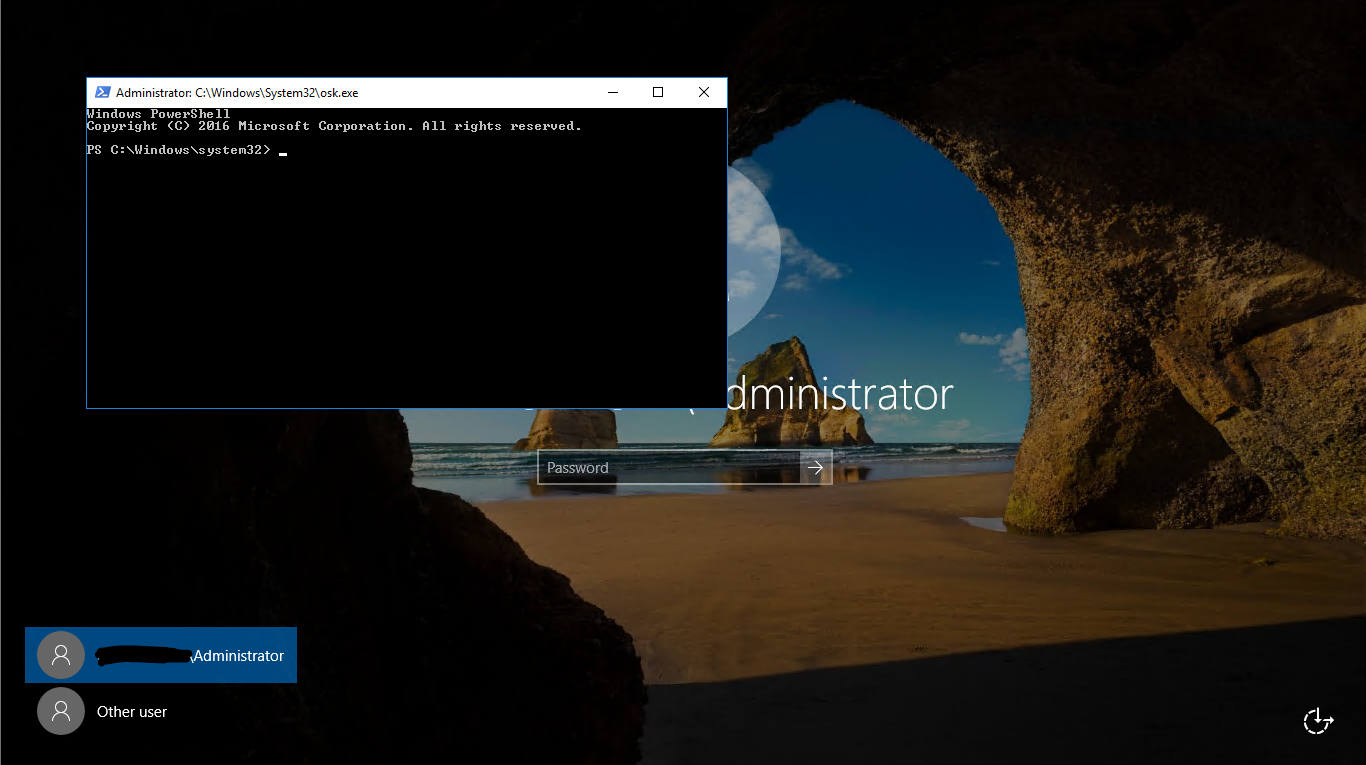
- Login to server with the new password – just to test that it is working.
- Reboot the server and redo all the steps from 1 to 5, but in the way to put back all things in the original state. You need to replace original onscreen keyboard:
- Go to C:
- Type cd \Windows\System32
- Type del osk.exe
- Replace a file with ren osk.old osk.exe
- Reboot the server.
That’s all. I recommend you to disconnect the server from the internet in the time you are doing these steps. In the same way you can access to the PowerShell window, it can be accessed by anyone who can see logon screen!