Yes, in some cases this can be a problem. As is true, that if you are connected in remote to a computer, you can just press CTRL + ALT + END and start a new window in Task Manager, this becomes more difficult if you are remote connected in remote session. In This case this shortcut will not work.
Well, the problem is pretty easy to solve:
Run PowerShell as Administrator on some other computer and find the session ID with command:
QUSER /Server:ServerName
You will see all active connections and here you will find also a SessionID for the connection that you want to kill.
Now you know your SessionID and finaly you can kill the connection. This can be done in two ways:
– As command in CMD: logoff Your_SessionID /server:ServerName
– In PowerShell: Invoke-RDUserLogoff -HostServer ServerName -UnifiedSessionId SessionID
Well, now you lose your session and if you will connect to that server, you will have a new session with your CMD window opened.
Category: Management
NIC Location on domain controller shows Public network
It could happen. I saw this issue couple of times, not only on domain controllers, but also on other domain joined computers.
The cause of this problem is the Network Location Awareness service. We know, that this service is recognising network location based on gateway and is trying to locate AD server thru port 389. Well, when gateway is changed or no server connection true port 389 is available, we have a new network location – by default it is Public.
Anyway, it can happened that NLA service starts before the AD services are started (or before DC is reachable on a non DC server). In this case, we will have public network profile on DC or domain joined computers. If firewall is enabled, most of network services will not run as the firewall for the Public profile is almost closed.
We have few possibilities to solve this situation. Maybe the most simple way is to restart the server, but I don’t know if I can restart the server at this moment and what was the original cause of the problem – maybe it will reappear. The second option is to disable / reenable the NIC adapter and in most cases, it will solve the issue. We will get the same result if we just restart the NLA service – this is a better way.
In some cases, you cannot connect to the computer for some reason. In this case, I use PowerShell remote session to solve the problem.
Here are the steps:
Enter-PSSession ComputerName (establish connection to computer with the problem)
Get-NetConnectionProfile (this will show you your current location profile – if this is the source of the problem, the location will not be Domain)
Restart-Service nlasvc (this cmdlet will restart NLA service; after this step you should see Domain network profile)
Get-NetConnectionProfile (just to check if the solution works)
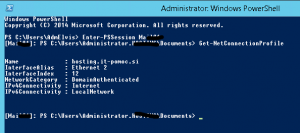
Exit-PSSession (disconnect form the remote computer)
Based on my experience, this solution works always. Some administrators also suggest to change start option for NLA service to Automatic (Delayed Start). I am not sure if this is a good solution; be careful with it. Maybe you can do it in cases where this error is frequent (better: search for the original cause and solve the problem)
PowerShell license tips
Well as I know many users are trying to find Windows key with some key viewer software. Nothing wrong, but this software is not always “nice” and can do something else than just show you a key. Of course, with Windows 8.1 and Windows 10 you have many times a key in BIOS, so there is no need to search for it.
Anyway, if you feel better when you have a key printed on a piece of paper, you can do that simply with one PowerShell cmdlet:
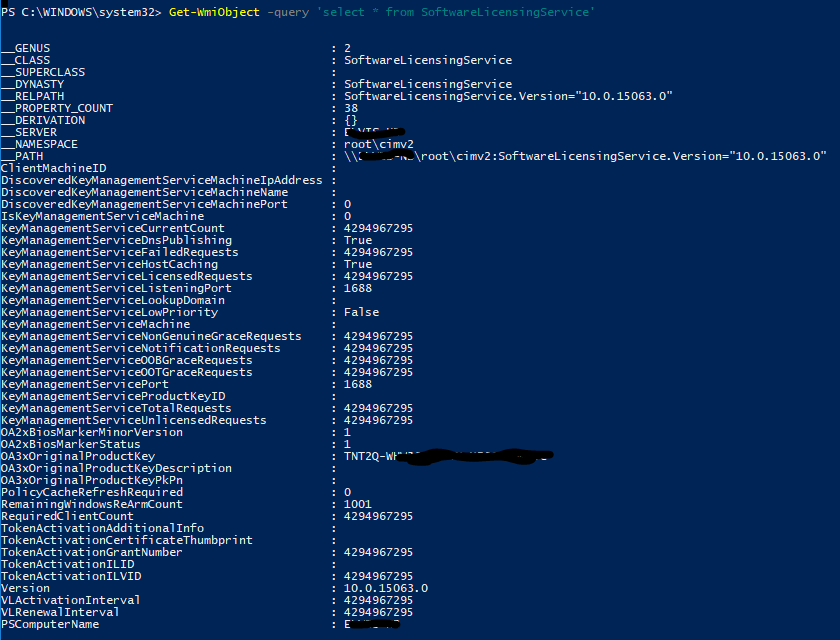
Get-WmiObject -query ‘select * from SoftwareLicensingService’
This will show you more than only a key. There are a lot of information on licensing, like KMS server, OS version, … In some cases it can be useful.
Windows ADK on Server 2016 – Unsigned driver?
If anyone tries to install the new Microsoft ADK (for Windows 10 Version 1703 – 10.1.15063) on Windows server 2016, you receive the error that a driver is not digitally signed. Well, Microsoft drivers are not signed? Something is wrong…
Actually, according to this post, they really have a problem and there is a workaround with disabling the secure boot. But this is not recommended and is not aligned with best practices – so you don’t want to do it.
Anyway, this is the only way you can install ADK on server 2016 and I did it. I have removed the previous (broken) installation, disabled Secure boot and reinstalled ADK. After a successful installation, I reenabled Secure boot and things still went wrong. I was unable to mount ADK boot image (to use in SCCM or MDT). Well, in this post it is explained another workaround (yes, I know…). Set the registry as is explained and it should work. I just hope that all other functionalities in ADK now are working OK.
WannaCrypt Malware
Of course you have heard about the new malware, which yesterday created a lot of problems in industry. Unfortunately it is not an unknown problem.
Microsoft released a patch for this type of vulnerability already in March, but it seems once again that administrators are not patching their systems.
So, if you haven’t patched your systems at least every month, if you haven’t patched your system from March, is time to do it. And don’t forget to have a good defense system (antivirus and other prevention mechanisms). Update them to!
You can find additional information in this link.
Here is a link to post how was neutralized and who did this.
Anyway, we have already a version 2.0; you can read about this version here.
Again, please patch your systems! This update will solve a vulnerability. And don’t forget: this is not the first malware who was written on known vulnerability – patch your systems constantly!
Additionally, please disable SMB1 protocol – it is not new that it is not secure. Here and here are some guidelines how to do it via GPO.